One can only imagine the wonders that lie in the crypto labs of organizations like the CIA or the NSA. They must contain machines of such complexity that no electronic device could resist their attempts to overcome the security built into their chips. Machines like these undoubtedly have price tags that only a no-questions-asked budget can justify, making their techniques unaffordable for even the most ambitious home gamer.
That could change, however, with this $500 DIY laser fault injection setup. It comes from Finnish cybersecurity group (Fraktal), who started a series of blog posts detailing how they built their open-source reverse engineering rig. LFI is similar to other “glitching” attacks we’ve covered before, such as EMP fault injection, except that it uses a laser aimed directly at a silicon chip to disrupt its operation, rather than a burst of electromagnetic energy.
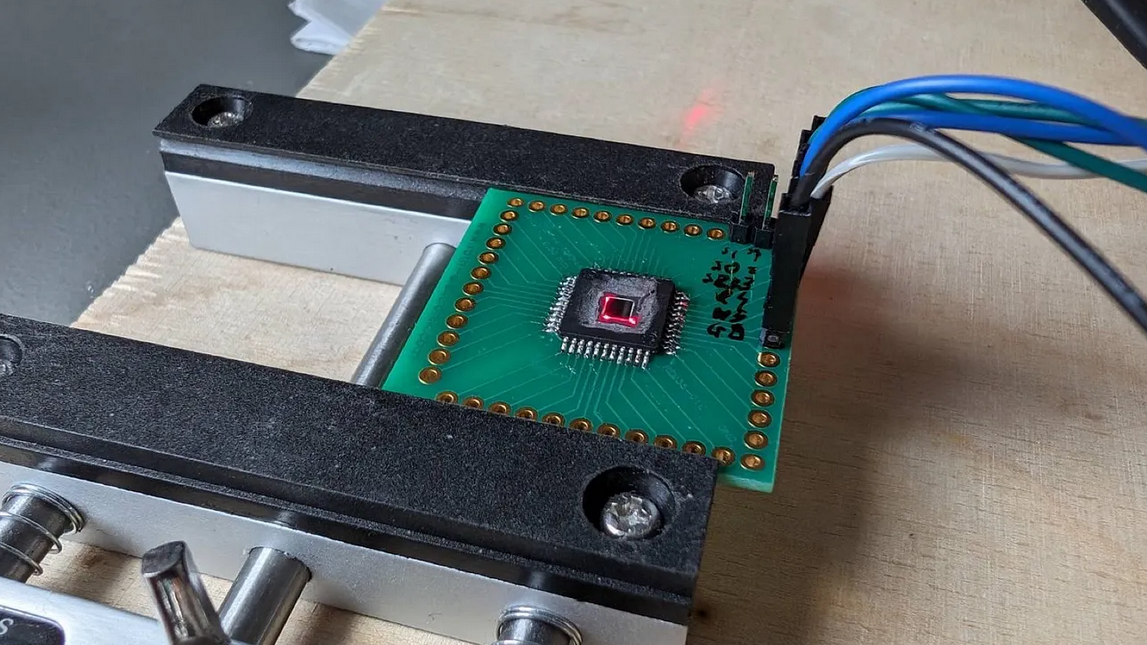
Because LFI requires the laser to be aimed very precisely at nanometer-sized elements of a bare silicon chip, nanopositioning is the biggest challenge. Rather than moving the device being attacked, the (fractal) equipment uses a modified laser galvanometer to scan an IR laser across the device. The galvanometer and optical components are all readily available online, and they’ve started a repo to document the modifications required and the code to put it all together.
Of course, this technique requires the chip to be exposed in the device being examined, but (Fractal) has made that pretty easy too. They include instructions for milling away the epoxy from the leadframe side of a chip, which is safer for the delicate structures etched into the top of the chip. The laser can then shine directly through the chip from below. For “flip-chip” packages like BGAs, the same milling technique would be performed from the top of the package. Either way, we can imagine a small CNC mill making the process safer and faster, though they seem to have gotten along pretty well with a Dremel.
This looks like a fantastic reverse engineering tool and we are very excited to see the rest of the story.
Thanks to (gnud) for the tip.