
Threat actors began using progressive web applications to impersonate banking apps and steal credentials from Android and iOS users.
Progressive Web Apps (PWA) are cross-platform applications that can be installed directly from the browser and provide a native experience through features such as push notifications, access to device hardware, and background data synchronization.
Using these types of apps in phishing campaigns allows you to evade detection, bypass app installation restrictions, and access risky permissions on the device without having to display a standard prompt to the user that could raise suspicion.
The technique was first observed in the wild in Poland in July 2023, while a subsequent campaign launched in November of the same year targeted Czech users.
Cybersecurity company ESET says it is currently tracking two different campaigns based on this technique, one targeting Hungarian financial institution OTP Bank and the other targeting TBC Bank in Georgia.
However, the two campaigns appear to be operated by different threat actors. One uses its own command-and-control (C2) infrastructure to obtain stolen credentials, while the other group logs stolen data via Telegram.
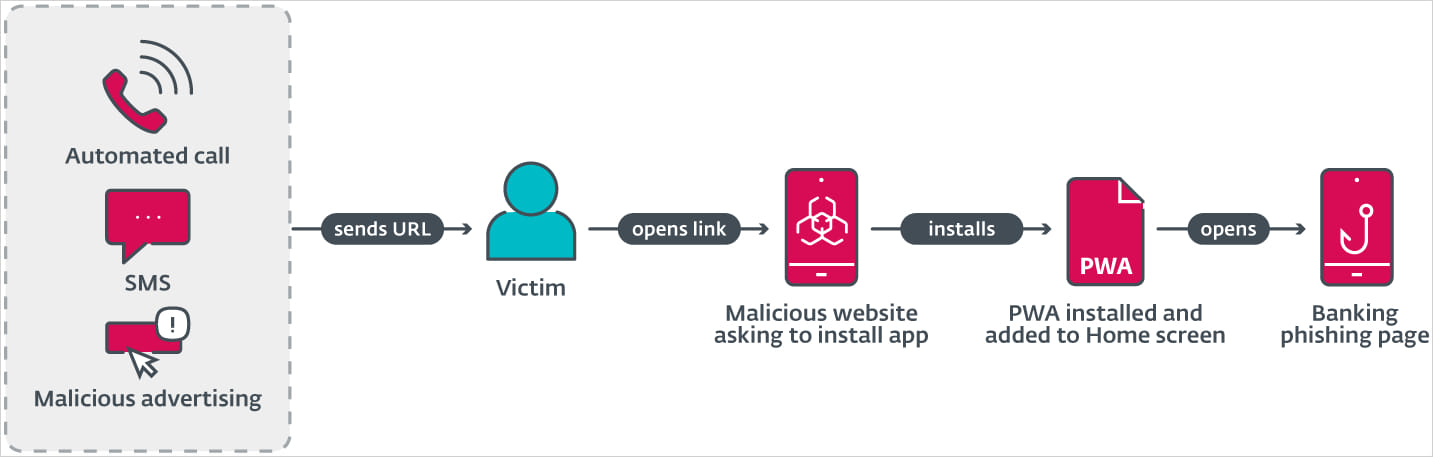
Chain of infection
According to ESET, the campaigns use a wide range of methods to reach their target audience, including automated calls, SMS messages (smishing) and well-crafted malvertising in Facebook advertising campaigns.
In the first two cases, cybercriminals trick the user with a fake message that their banking app is out of date and needs to install the latest version for security reasons, and provide a URL to download the phishing PWA.
Source: ESET
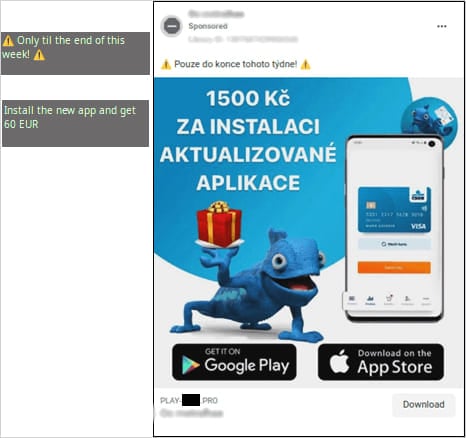
In the case of malicious social media advertisements, threat actors use the bank’s imitated official mascot to create an impression of legitimacy and promote limited-time offers such as cash rewards for installing a supposedly important app update.
Source: ESET
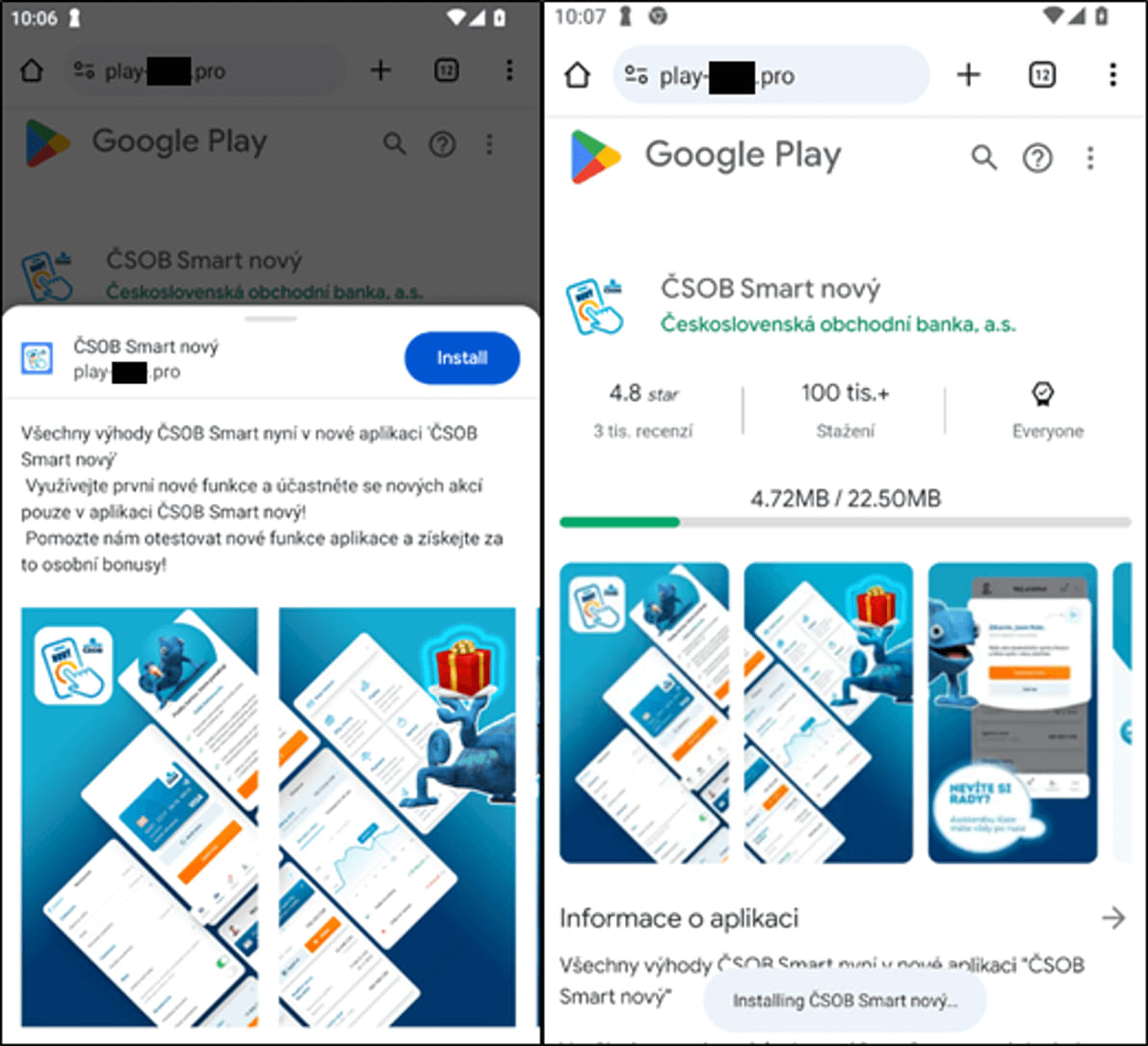
Depending on the device (verified via the User-Agent HTTP header), clicking on the ad takes the victim to a fake Google Play or App Store page.
Source: ESET
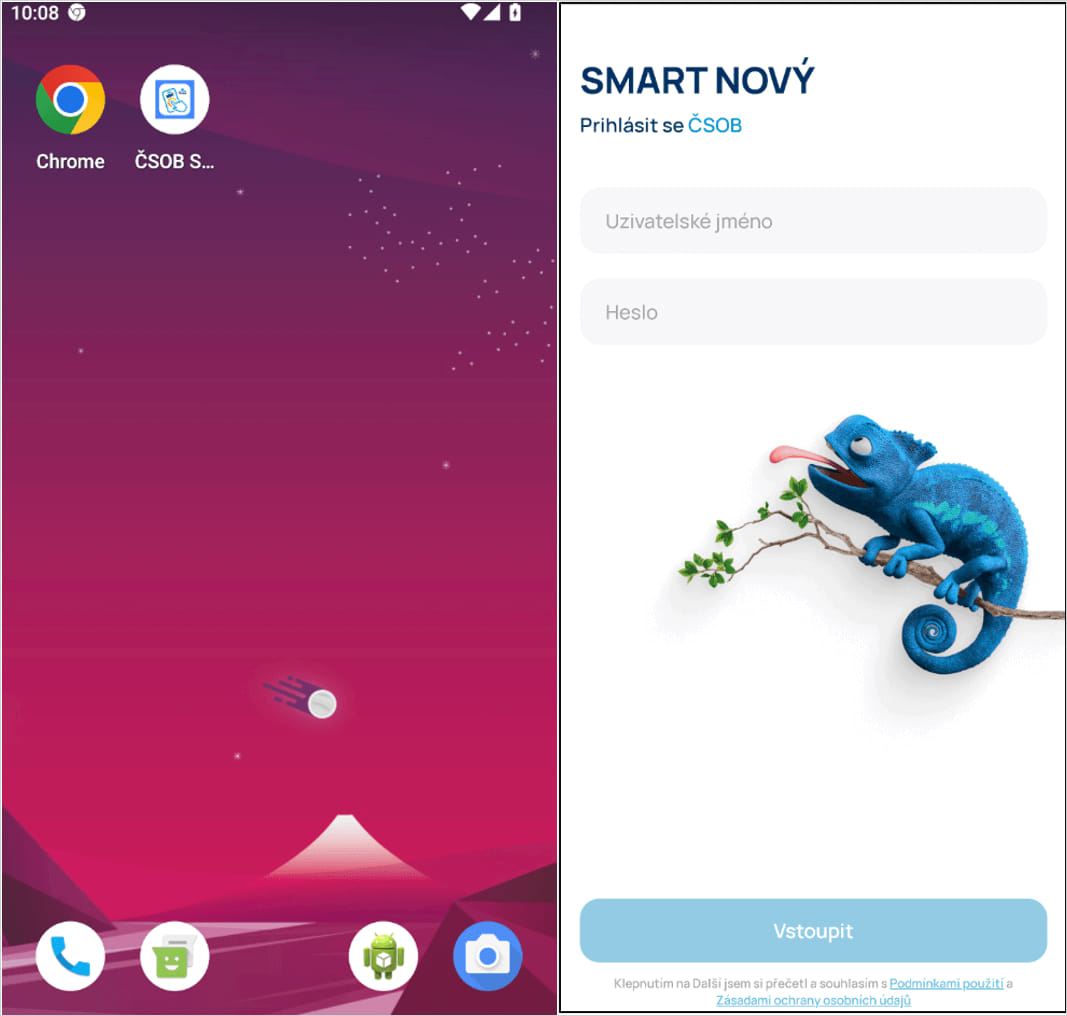
When the user clicks the install button, they are prompted to install a malicious PWA that pretends to be a banking app. In some cases, the malicious app is installed on Android in the form of a WebAPK – a native APK generated by the Chrome browser.
The phishing app uses the identifiers of the official banking app (e.g. the logo of a legitimate-looking login screen) and even lists the Google Play Store as the app’s software source.
Source: ESET
The appeal of using PWAs on mobile devices
PWAs are designed to work across multiple platforms, allowing attackers to target a wider audience with a single phishing campaign and payload.
However, the main benefit is that it bypasses Google and Apple’s installation restrictions on apps outside of the official app stores, as well as the “Install from unknown sources” warnings that could alert victims to potential risks.
PWAs can closely mimic the look and feel of native apps. This is especially true for WebAPKs, where the browser logo on the icon and the browser interface within the app are hidden, making it nearly impossible to distinguish them from legitimate applications.

Source: ESET
These web apps can access various device systems such as geolocation, camera and microphone through browser APIs without requesting them on the mobile operating system’s permissions screen.
Ultimately, PWAs can be updated or modified by the attacker without user interaction, allowing the phishing campaign to be dynamically adjusted to increase success.
The misuse of PWAs for phishing is a dangerous new trend that could reach new proportions as more cybercriminals realize its potential and benefits.
A few months ago, we reported on new phishing kits targeting Windows accounts using PWAs. The kits were specifically developed by security researcher mr.d0x to demonstrate how these apps can be used to steal credentials by creating convincing corporate login forms.
BleepingComputer has contacted both Google and Apple to ask if they plan to implement defenses against PWAs/WebAPKs. Once we receive a response, we will update this post with their answers.
